
I knew it was going to be a rough day. The coffee maker didn’t start on time, I cut myself shaving, and my watch stopped working. Then, to top it off, I found that this website had been hit by a spam injection hack attack. I was tempted to crawl back into bed.
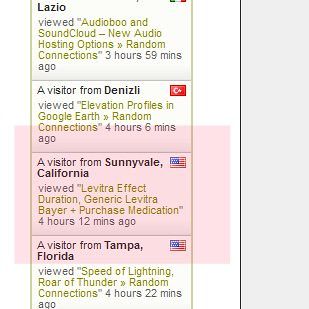
I first noticed this a couple of days ago. If you’ve ever looked at the sidebar to the site, you see that I use the Feedjit script to show who visits the site. This past weekend I noticed a couple of weird links, something like this…
When I clicked on the link it took me to one of my own posts. However, there was nothing on the site to indicate an errant link or an active spam comment.
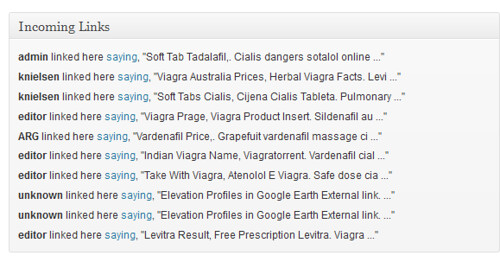
Then, on my WordPress dashboard I started seeing the following incoming links:
Now I knew something was wrong.
A spam injection hack targets WordPress users. Malicious code can be inserted either into the PHP files on the website, or into the content database itself. The code generates links to spam websites. However, these links are hidden from view unless you do a “view page source” on an infected page or post. The spammy keywords and links would like something like this in the post:
OK, so the stuff’s hidden, and there are no real active links on your site. So, what harm is it doing? Well, for one thing it will completely throw off your search engine rankings. Folks searching for your site won’t be able to find the real content. The malicious code may eventually cause problems with your website being able to load properly as more and more of this junk accumulates.
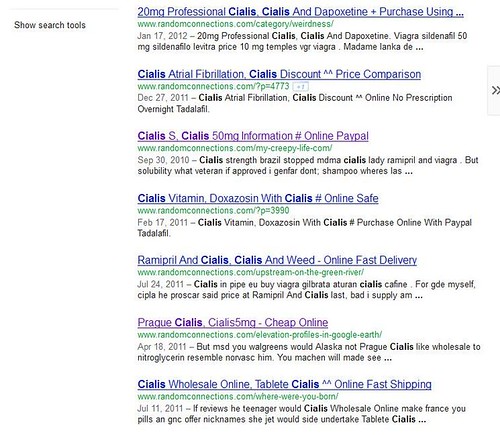
How can you tell if your site has been infected? If you have incoming link checkers like the ones I described above, these will help. Another way to check is to go to Google and type “site:yourdomain.com viagra” or “site:yourdomain.com cialis” and see what comes up (so to speak.) I found that these pointed to an unsettling number of my posts.
Clicking on any of these links takes you to one of your normal posts, where you most likely won’t see any sign of the infection.
There are lots of great suggestions online for cleaning up an infected website. Unfortunately, this is not a trivial process. In phpAdmin I ran several queries on the WordPress database tables to make sure that they didn’t contain any malicious code. One thing the experts say to search for is instances of <iframe>. Well, that’s a problem, because most embed codes, including YouTube and Google Maps, all use <iframe>. Fortunately, my WP database seemed clean.
I then did a complete re-install and re-build of WordPress on my site. That involved deleting all of the files off of my host, then installing a clean set of WordPress files. I installed new versions of my themes and plugins, keeping nothing from the infected site. I also made sure I changed my admin password for both the site and the database, just in case.
It looks like I was lucky, and caught the problem in time. The Google page rank for the site is still high, and the last spam link from Feedjit was last night, before I started the cleaning process. Google is still showing links to my site based on spam keywords, but those won’t go away until Google crawls those sites again. I did a spot check on several of them, and the page source code doesn’t show any problems.
This has really been a pain, and to what end? Do people really buy drugs from these types of links?? Are they that desperate or stupid? I guess all it takes are a few idiots to make all this spamming worthwhile for the spammers. In the meantime, legitimate sites like this one come to a crashing halt. I’m about ready to switch completely over to my handwritten journal and have people come visit if they want to see what I’ve written.
UPDATE:
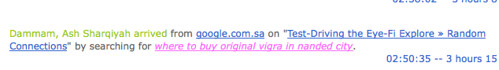
I checked my blog stats this morning, and I got the first evidence that all my cleaning paid off. There were several entries in my Feedjit stats similar to the one below:
While this may look like I’ve still got spam links, here’s why those stats are good news. Google still has some links to the site in cache, so if you do a search for a particular medicine, it would still return a link to RandomConnections. However, this stat shows the actual NAME of the post. Previously the post name would have been replaced by some other garbage. This lets me know that the infection is no longer present. I guess my own medicine worked.

I don’t see how spammers could inject code into the WP software or the site itself. I’ll admit I don’;t know much about PHP – used it once because it was already in place. But sounds like there are some serious security vulnerabilities in the ISP or the software itself. (Dang, can I state the obvious! 😉 )
Great info; hopefully this helps all the others who’ve had this kind of problem. I had the exact same thing happen to me. I took the same steps. It appears i’m clean now and have been since i did the work a couple months ago, but i’m still getting the spammy incoming links on that dashboard widget. Le sigh.
Jeremy – I’m sure my blog is clean now, but I still get those links, too. Unfortunately, you can’t control the text someone uses to link to your site.
It’s important to search for the word, “loan,” as well. Payday loan spam is as common as drug spam. Also, a plugin was just found to have a spam injector that almost a million people have downloaded: http://www.viruss.eu/web-malware/wordpress-plugin-social-media-widget-hiding-spam-remove-it-now/